Computer Law & Security Report Vol. 20 no.4 2004, pp. 281-287
Thierry MAILLARD & Teddy FURON
First publication : July 2004.
This article aims at linking researches in copyright law and in multimedia security. It presents the core legal issues in the field of content protection and proposes a renewed approach to copyright enforcement. Stating the necessity of tackling the exemptions to copyright from a technical-based approach, it introduces the notion of Digital Rights and Exemptions Management Systems (DREMS). The authors emphasize the need for moving into such DREMS protection schemes and examine the possibility to implement the “balance of interests” within the protection devices.
Digital technologies have introduced new ways of reproducing, storing and distributing multimedia content. This has allowed right holders to develop new services and business models, but it also has given birth to large-scale piracy, involving the recourse to two complementary means: law and technique. During the past few years, the enforcement of copyright has encouraged research work in watermarking and cryptography, resulting in many technical developments. But most of the currently considered solutions are grounded on a misconception of copyright. While technical means of protection are commonly conceived as a safe sheltering for works, any leeway retained by consumers in the use of content is considered as an unbearable potential security flaw.
This over-defensive approach to copyright is irrelevant and fraught with consequences for the future of the content industry. Copyright law is not one-sided. It protects authors and investors’ interests, but also users’ ones, striving to strike a proper balance of interests. Whereas tensions between producers and users are becoming dangerously acute, it is fundamental to integrate those aspects into technical protection designs. This article, suggesting new avenues of designing Digital Rights Management (DRM) systems, is a plea for a return to a sound situation where law strikes a proper balance that technology maintains in equilibrium. It offers an accurate picture of the relationships between researches in law and in multimedia security, linking the approaches to assess both the security and durability of technical means and the feasibility of the current legislative trends.
A. The balance of interests
Each copyright system is – more or less explicitly – based on the quest for a workable balance between private rights and the public interest, with the view of promoting learning, culture and development. This idea of balance of interests clearly appears in many laws and international conventions such as the US Constitution, the WIPO Treaties of 1996 [1] and the European Union Copyright Directive (EUCD) [2]. Three social interests are thus to be taken into account:
• The authors’ interests. It is easily understandable and only natural that authors receive an appropriate reward for the use of their work. This first objective of copyright, undoubtedly the most well known and best understood, is definitely essential to ensure both independence and quality of creation.
• The investors’ interests. The protection of investment is an objective very close to the above-mentioned one. Authors usually find their financial supports from investors (producers, editors etc.), who can justly expect a return-on-investment.
• The public interests. The first two objectives must not impede the satisfaction of the public interest. Each copyright system strives – to various extents – to give users some leeway, by delimiting the scope of exclusive rights and by exempting from authorization certain uses. In the first case, it is often referred to as “boundaries” or “limits”: it consists in making a clear distinction between what is part of the “reservation zone” and what is, by its nature, freely usable (e.g. ideas, facts, works fallen into the public domain, unoriginal works). In the second case, it is referred to as “exemptions” or “limitations”. It covers a very large range of situations, each national copyright law having its specificities. However, most copyright systems know the same types of exemptions, either through a limited list or through a general provision such as fair use. Some great types of exemptions are commonly distinguished [3] personal use, news reporting, quotation and criticism, science, educational uses, archival storage, library and museum privileges, administration of justice and other government uses.
B. The copyright systems imperilled
During the last two centuries, copyright systems have succeeded in striking a proper balance of interests. Yet, this subtle equilibrium has been overturned with the advent of the digital age, to such an extent that the whole fabric of copyright threatens to collapse. Four significant periods can conceptually be distinguished, corresponding to the successive states of the balance of interests (see Figure 1 below).
• The analogue age. Copyright systems have been built and balanced with regard to the specificities of the analogue world, especially the bond between content and its physical medium. As regards many exemptions, lawmakers have endeavoured to weigh up the prejudice caused to right holders with the cost or the practical difficulties pertaining to the enforcement of rights. Private reproduction was recognized as an exemption mainly because, at the time, it was time-consuming and generated a loss of quality.
• The digital age. The advent of the digital age has substituted the notions of immateriality, ubiquity and instantaneity for those of materiality, territory and duration. This has exposed right holders to the risk of a de facto exhaustion of the whole content market by the very first copy delivery, gravely questioning the effectiveness of rights. A quick reaction was thus needed to restore the balance and in December 1996 the WIPO Treaties were adopted.
• The WIPO Treaties. These fundamental treaties have introduced legal protection for technological protection measures (TPMs) against circumvention. These texts only meant fix a general framework, giving substantial leeway to the national legislators for their implementation, especially in determining the acts in connection with the circumvention to be prohibited [4] and the way to deal with the question of exemptions [5]. So the United States adopted in 1998 the DMCA [6] introducing in the Copyright Act of 1976 a twofold protection for TPMs. Section 1201 prohibits both the act of circumvention and the preparatory activities as regards TPMs controlling access, whereas it prohibits the preparatory activities only as regards TPMs protecting a right of a right holder. The EUCD implemented the WIPO Treaties in a similar way. Copyright systems are thus moving in the direction of a legal and technical overprotection for right holders, which threatens the exercise of copyright exemptions. Although each system has provided its legal scheme for guaranteeing this exercise, we believe that only technically consistent schemes – i.e. allowing the exercise of exemptions without undermining the DRM security scheme – will be viable.
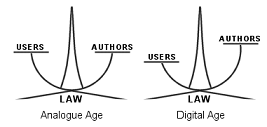
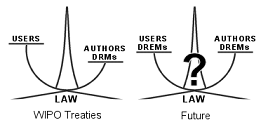
Figure 1: Successive states of the balance of interests
• The Future. Whereas debates around copyright are dangerously turning into an overpassionate crusade, the challenge for the future is to achieve a workable balance between the interests, where TPMs enforce at once the protection of content and the exercise of the exemptions. We believe the success of this enterprise lies in the following new concept: Digital Rights and Exemptions Management Systems (DREMS). The next sections deal with the feasibility of such systems.
C. Methodology
This section proposes methodological considerations useful to design the future DREMS. The first requirement is the determination of a set of norms that can be used to define the applicable framework which can then be refined to make DREMS feasible.
1. Determination of the normative framework
It is necessary to determine the legal norms to be taken into account as a basis for the design of DREMS. The choice of the normative framework has to be general enough to take due account of most copyright systems and precise enough to be technically implementable.
Two main legislative approaches can be distinguished. In Roman law systems (for instance in France), the exemptions system is usually “closed”. The exemptions are analytically defined in a limited and descriptive way, whereas the author’s exclusive rights are generally synthetically defined. On the contary, in Common law systems (for instance in the USA), the definition of rights is analytical and the exemptions are synthetically determined. The epitome of such an open system is the fair use system (Section 107 of the US Copyright Law), which provides some factors to be considered to determine whether a particular use is fair. Such open systems, although legally valuable, seem too flexible to be effectively implemented in DREMS, notably because they are mostly based on the intended purpose underlying acts and consequently hard to handle technically [7].
The ideal thing would be to put together a precise and comprehensive framework, taking due account of the legal traditions of all national copyright systems. Due to the difficulty of this task, it may be simpler – and still admissible – to refer to a more restricted framework such as the list of 21 exemptions provided by the EUCD, which corresponds to all the exemptions existing in the European States and which also roughly coincide with the concrete acts authorised under the fair use system.
2. Refinement of the applicable framework
The conciliation between TPMs and exemptions is mainly a practical issue. It consequently appears essential to characterize the exemptions from a physical-based approach. Exemptions are legal objects, but they are also material acts. By determining the technical specificities of these acts, one can establish the requirements to deal with these legal objects through DREMS. We propose two approaches.
The first is based on making a clear distinction between convenience and necessity. It must be kept in mind that DREMS simply have to facilitate the acts strictly requisite to the exercise of the exemptions; they do not have to enable a convenient exercise [8]. To illustrate this point, one can imagine a TPM preventing digital copy and a user willing to make a copy in order to benefit from an exemption. If the exemption can be exercised with analogue copy – for instance a screen capture with a camcorder – there is no reason to enable a digital reproduction too, simply because it is more comfortable. This basic comment, although stating the obvious, is definitely a key to designing DREMS and dealing with the question of the exemptions in the digital era.
The second approach consists in building a technical-based typology of exemptions. A careful examination of the exemptions from a physical-based approach shows that, beyond the apparent diversity, many of them are similar when considered as material acts. One can classify exemptions by technically significant types so that it will decrease the effort made on designing DREMS. Once the technical requirements for each type of exemption have been characterized, one can consider future exemptions based on this classification.
We consider below six dichotomous criteria useful to classify the exemptions:
• Materiality / immateriality. It is essential to ascertain whether the exercise of the exemption requires a material use of content. Many exemptions do not materially conflict with TPMs and there is no need to implement them. Many copyright laws provide, for instance, an exemption with respect to uses for the purpose of caricature, parody or pastiche. Those purposes do not require reproduction or any other material act: the use is strictly intellectual.
• Individual / collective beneficiaries. The requirements also depend on the nature of the beneficiary. Collective users such as libraries, hospitals, prisons, museums or archives are clearly identified, localized, trusted and in a relatively small number. It makes the agreements between them and right holders more easily admissible as the requirements for those exemptions are by this fact not so drastic.
• Public / private use. The required means of control are not the same depending on whether the use is public or private. Some exemptions are to be publicly exercised. The right holders or their representatives are then generally able to check “in the field” the compliance of these uses with legal provisions. There is consequently no need to seek for a b technical protection. On the contrary, privacy law opposes such direct control when exemptions are privately exercised. In this case, the recourse to TPMs – and therefore to DREMS – forces itself. This criterion is close to the precedent one.
• Whole / extract. Another point to consider is whether the exercise of the exemption envisages any extraction. Some exemptions, such as quotations for the purposes of criticism or review, are restricted to the sole use of excerpts of works, to the extent required by the specific purpose. As shown in the following section, this specificity is technically significant.
• High / low frequency. The more frequent the exercises of an exemption, the more an implementation in DREMS is needed. Some exemptions are to be exercised without delay. See, for instance, article 5.3 j) EUCD concerning the uses for the purpose of advertising the public exhibition or sale of artistic works. The frequency of such cases permits agreements with right holders.
• Material conditions / intended purpose. Whereas many exemptions refer to material conditions, some exemptions are solely based on purpose. For instance, article 5.2 b) EUCD provides an exemption to the reproduction right “in respect of reproductions on any medium made by a natural person for private use and for ends that are neither directly nor indirectly commercial.” The requirements are very specific since the admissibility of the exemption cannot be appreciated at the time of the act of reproduction: the public or private nature of a use is generally revealed a posteriori.
These are the most obvious and important criteria. Designing DREMS naturally calls for more numerous and accurate criteria determined by a very close examination of legal systems through a technical prism. As yet, no fully operational solution is anticipated. In the following section, we offer some suggestions on how to put this “technolegal” methodology into practice.
D. Implementing the balance of interests
This section investigates the technical difficulties related to the implementation of DREMS. It deals with two important classes of exemptions, each of them having their proper technical specificities. A short introduction first describes the three main types of technical protection means available.
1. Technical background
There are three kinds of technologies pertaining to the protection of data. These TPMs do not manage rights and exemptions on their own; they are only security bricks. A DREMS designer can build with these bricks a system architecture that will globally enforce rights and exemptions.
The first kind of TPMs protect the access to the data. It can be a physical barrier that prevents users from reading the bits stored on the medium. Thus, proprietary formats preclude the use of standardized access devices. Complex software solutions forestall pirates from tappping the data in the memory of computers. Another example is the infringement of the Compact Disc standard preventing playback by CD-ROM drivers of personal computers. Hence, dishonest users cannot copy the music tracks on hard disk or burn them on blank discs.
In the second kind of technology, encryption does not preclude the access to the data but the meaning of their semantics. The bits are encrypted or scrambled according to a secret key. This implies the existence of a secure place to safely store this secret especially at the user side. The most trusted piece of hardware nowadays is a smart card. Encryption is not the only useful cryptographic primitive. Authentication allows two devices to shake hands, prove their identity and agree on a random key ciphering the data to be exchanged.
Data hiding is the last line of defence. Physical barriers and encryption are good TPMs as long as content remains digital. Unfortunately, the weakest link in the delivery chain is the analogue link. Video has to be rendered on a display. Audio has to be played through loud speakers. The pirate, as a dishonest user, can play the content, record these signals, digitise them, and distribute unprotected files. This threat is called the “analogue hole”. Watermarking is regarded as a promising technology to solve this problem. A watermark is a weak signal added in the video pixels or the audio samples in a non-perceptible way. This signal is a carrier transmitting hidden data. It is robust if devices retrieve the hidden bits from content that as undergone some processing like compression, scaling, or colour adjustment. Thus, a robust watermarking binds a piece of content with some data. Depending on the application, the hidden bits code the identity of the copyright holder with, an international serial number, copy control information or a signal warning that the piece of content is protected. There is a trade-off between the amount of hidden data and the robustness of the watermark.
The compliant world is defined as the set of devices which conform to a particular DREMS. Legacy appliances, devices free from any DREMS, the hacked devices, and the ones compliant to another DREMS constitute the rest of the world, also called the uncontrolled sphere. The goal of a DREMS then is to manage protected content without any leakage into the uncontrolled sphere. As far as we know, for multimedia content, this is not feasible with the above-mentioned technical protections. As already stated, a dishonest user can record analogue signals and digitize them. It is impossible to forbid their rendering in the uncontrolled sphere. Yet, it is possible (and might be sufficient) to forbid it in the compliant world.
2. Private reproduction
The first class of exemptions here considered is the reproduction for “private use”, characterized by its privacy, high frequency, and by the fact that it covers individuals’ uses. It is certainly the hottest topic in copyright. Although content providers and manufacturers launched hand in hand audio CD during the eighties and video DVD in the nineties, the simple record button on digital devices has given birth to a rampant dissension among the entertainment industry. As the number of anti-copy CD systems increase, many consumers resort to a so-called “right to space-shifting” (e.g. copying CDs on MP3 portable devices) to be used in an unlimited, unconditional manner. Yet, the main argument stemming from the methodology above exposed is that the exemption for private reproduction, which is certainly not grounded on a fundamental right, is admissible only if its exercise remains limited. The quest for user-friendliness must not ruin the balance of interests. The simplest method is to forbid copying using the above-mentioned means. Unlike the game industry, proprietary formats are not recommended in the content industry as it conflicts with the need for standards to be adopted by content providers and manufacturers. The use of encryption is the most popular line of defence.
Video DVDs are encrypted with CSS; CPPM system protects audio DVDs. The second concern is the analogue outputs of compliant devices. The Macrovision system prevents the dubbing on VHS tapes. Watermarking is another solution, except that it won’t preclude the copying but the playback on compliant devices [9]. The watermarking doesn’t need to carry any information. It is just an invisible signal, warning devices that this piece of content is protected. Hence, in the compliant world, encrypted and watermarked content is legal; watermarked content in the clear is regarded as a forged copy. Facing the need of the manufacturer to sell new devices, a discussion concerning DVD video recorders between content providers, CE and IT industries started in 1997 [10]. The outcome has been a new approach so-called CGMS (copy generation management system) based on four copy control options: “copy never”, “copy free”, “copy once” and “no more copies”. Content providers are in charge of giving one of the three first states to original content. Users make copies of content whose status is “copy free” or “copy once”; the copy of the latter is then labelled “no more copies”. These rules merely reflect the exemption of private use. This underlines the difficulty of enforcing with technical means an exemption based on the intended purpose underlying the act. Moreover, this system has many pitfalls: there are at least three different encryption schemes (for prerecorded content, for digital transmission and for storage) and the main hardship is the management of the private keys. A strategy closer to the exemption is to bind the copy to the user’s home. SmartRight is such a DREM platform [11].It is assumed that the user’s devices are connected in a home network and that they share a secret key in common. Separate home networks have different secrets. When a copy is allowed, the device encrypts it with the secret and stores the ciphered version on a medium. The user can make hundreds of copies of the same piece of content. It doesn’t matter as the copies can only be decrypted by a device from his network. Indeed, the technical difficulty is the management of the secret. For instance, one solution is to automatically share this secret in a secure way with new devices plugged in the network. By this approach, only one encryption scheme is used. The last strategy allows copying with a loss of quality as occurs with some CE CD audio recorders do. This is not a bit-to-bit copy as audio content is going from digital to analogue, then, converted back to digital before being burned on a blank CD. This mimics the former spirit of the copy on analogue tapes.
3. Quotations and excerpts
A second significant class, here referred to as “quotations and excerpts”, concerns exemptions requiring frequent excerpts from works. It mainly concerns quotations for criticism or review and, to some extent, illustrations for teaching or scientific research. Imagine a researcher in the field of cinema wants to quote a passage from a movie in order to analyse crucial detail necessary to understand the producer’s works. At first glance, the solution is easily found. The DREMS permits excerpts from movies limited in duration, size, and/or quality. Things are more complex, however, if the DREMS also has to deal with the exemption of “private use”. In this case, the excerpt, which is a piece of approved watermarked content, is not played back (see the above subsection). But watermarking technology is not perfect. A watermark detector needs to observe a minimum amount (duration, size, quality) of content to reach a decision. For instance, the decision rate for video DVD watermarking has been set to ten seconds. The question then is to match this minimum amount of content for detection with the permissible fair amount for quotations. The three parameters must be taken into account. Some users will need only one image in full quality to show a detail of the scene, others will need a long excerpt at low quality.
The final issue is the possible leakage due to the exercise of this exemption. A dishonest user may forge permitted copy of the work mixing back several excerpts. The only counter-attack the authors are aware of is found in the paper of C. Herley [12]. A still image is served to the client in parts. The parts are imperceptibly modified in such a way that the alterations ensure that putting the parts together is extremely difficult without there being a clearly visible distortion. Thus, the client can view any excerpts in detail, but is unable to obtain a usable copy of the whole image. This work is a serious avenue of research but it isn’t sufficient, as C. Herley supposed the excerpts are produced by the same server. The conclusion is that the state of art of multimedia security is not able to build a secure DREMS for the “quotations and excerpts” exemption.
E. Conclusion
The guarantee of the exemptions becomes a new security issue in the design of DRM systems. Whatever the particular solutions adopted by national legislations, the implementation of the balance of interests through DREMS will be a fundamental issue in the coming years. We have exposed a methodology to address this issue, through a close partnership between law and multimedia security.
Striking a proper balance of interests is definitely a necessity; but necessity does not mean feasibility. It is likely that some exemptions will appear incompatible by nature with the technical protection and won’t therefore be considered in DREMS. The solution – if it exists – then depends on lawmakers, who must appreciate the need for an adequate legal reponse to the underlying needs of each exemption. Researchers in multimedia security should have a closer look at these legal issues. But lawmakers would also be well-advised to avoid grounding laws on technical infeasibilities by keeping up with research work in multimedia security. Building bridges between law and technique is fundamental for the future of copyright.
[1] WIPO Copyright Treaty and WIPO Performances and Phonograms Treaty, adopted by the Diplomatic Conference on Dec. 20, 1996. Available at: http://www.wipo.int/copyright/en/treaties.htm.
[2] Directive 2001/29/EC of the European Parliament and of the Council of 22 May 2001, Official Journal L 167, 22/06/2001 p.0010 – 0019, available at: http://europa.eu.int/comm/internal_market/en/intprop/docs/index.htm.
[3] See B. Hugenholtz, “Fierce creatures - Copyright exemptions: Towards extinction?” in IFLA/IMPRIMATUR Conference, “Rights, Limitations and Exceptions: Striking a Proper Balance”, Amsterdam, 30/31 October 1997.
[4] That is to say the act of circumvention itself and/or the preparatory activities (manufacturing, distributing, selling, advertising etc. any means of circumvention or providing related services).
[5] See J. de Werra, “The Legal System of Technological Protection Measures under the WIPO Treaties, the DMCA, the European Union Directives and other National Laws”, Revue Internationale du Droit d’Auteur, No. 189, 2001.
[6] Digital Millenium Copyright Act, Pub. L. No. 105-304, 112 Stat. 2860 (1998). Available at http://www.loc.gov/ copyright/legislation/dmca.pdf.
[7] See the mixed conclusions of Fair Use by Design?, Workshop at Computers, Freedom, and Privacy, San Francisco, CA, April 16, 2002. Available at: http://www. cfp2002.org.
[8] See P. Sirinelli, “The scope of the prohibition of the circumvention of technological measures: Exceptions”, ALAI Conference, Adjuncts and Alternatives to Copyright, Columbia University, New York City, June 13-17. Available at : http://www.alai-usa.org/default.htm.
[9] See M. Maes, T. Kalker, J.-P. Linnartz, J. Talstra, G. Depovere and J. Haitsma. “Digital watermarking for DVD video copy protection”. in Signal Processing Magazine, 17(5), September 2000. .
[10] DVD Copy Protection Technical Working Group, http://www.cptwg.org.
[11] SmartRight technical white paper, Thomson, available at: http://www.smartright.org/SMR_WhitePapers/.
[12] See C. Herley, Securing Images Online: a Protection Mechanism that does not involve watermarking, IEEE Int. Conf. on Image Processing, Vancouver, Canada, Sept. 2000.